利用virmach或者其他家的垃圾小鸡配上dropbox备份数据,好处在于成本极其低,一年甚至不到5刀!比没有80端口的NAS强多了
~使用bitwarden_rs搭建并每天备份两次到dropbox保证数据安全。
~理论上能跑docker就行,我搭建在virmach 1c384mb的小鸡上
~搭建环境为Centos7,只要能装docker就行。
~bitwarden的app和浏览器插件可以在对应的应用商店里找到,自动填充非常方便。安装后可以在设置里填自己的域名。
yum -y install docker systemctl enable docker systemctl start docker curl -L https://github.com/docker/compose/releases/download/1.25.0/docker-compose-`uname -s`-`uname -m` -o /usr/local/bin/docker-compose mkdir /usr/local/bitwarden vi /usr/local/bitwarden/config.env vi /usr/local/bitwarden/docker-compose.yml cd /usr/local/bitwarden docker-compose up -d
config.env
SIGNUPS_ALLOWED=true DOMAIN=https://xxx.com DATABASE_URL=/data/bitwarden.db ROCKET_WORKERS=10 WEB_VAULT_ENABLED=true ADMIN_TOKEN=wwwwwwwwwwwwwwww WEBSOCKET_ENABLED=true
version: '3' services: bitwarden: image: bitwardenrs/server:latest container_name: bitwarden restart: always volumes: - ./data:/data env_file: - config.env ports: - "9999:80" - "9998:3012"
docker-compose.yml
- version: '3'
- services:
- bitwarden:
- image: bitwardenrs/server:latest
- container_name: bitwarden
- restart: always
- volumes:
- - ./data:/data
- env_file:
- - config.env
- ports:
- - "9999:80"
- - "9998:3012"
DOMAIN填自己的域名,需要HTTPS。
ADMIN_TOKEN为管理面板密码,推荐使用“openssl rand -base64 48”生成。
SIGNUPS_ALLOWED=true,此项控制注册,只想自己用的话注册后可以改为false。
然后通过nginx反代开启SSL
由于vir的网络非常垃圾,建议去cf里生成orgin证书,套上cf食用。这样可以不用考虑源站证书续期
server
{
listen 80;
server_name pw.xx.com ;
return 301 https://$server_name$request_uri;
}
server
{
listen 443 ssl http2;
#listen [::]:443 ssl http2;
#listen [::]:80;
server_name pw.xx.com ;
ssl_certificate /xx.crt;
ssl_certificate_key /xx.key;
server_tokens off;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers on;
ssl_ciphers "EECDH+AES128:RSA+AES128:EECDH+CHACHA20:EECDH+CHACHA20-draft:EECDH+AES256:RSA+AES256:EECDH+3DES:RSA+3DES:!MD5";
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 1d;
ssl_stapling on;
ssl_stapling_verify on;
resolver 8.8.8.8 8.8.4.4;
resolver_timeout 10s;
add_header Strict-Transport-Security "max-age=63072000;includeSubdomains; preload";
add_header X-Frame-Options DENY;
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection "1; mode=block";
client_max_body_size 128M;
location / {
proxy_pass http://localhost:9999;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location /notifications/hub {
proxy_pass http://localhost:9998;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
}
location /notifications/hub/negotiate {
proxy_pass http://localhost:9999;
}
# Optionally add extra authentication besides the AUTH_TOKEN
# If you don't want this, leave this part out
location /admin {
# See: https://docs.nginx.com/nginx/admin-guide/security-controls/configuring-http-basic-authentication/
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_pass http://localhost:9999;
}
access_log /home/wwwlogs/pw.xx.com.log;
}然后vi /etc/rc.d/rc.local在最后加上/usr/local/bin/docker-compose -f /usr/local/bitwarden/docker-compose.yml up -d
这样开机就会自动启动bitwarden
访问https://你的域名/admin可以进去管理面板
到这里bitwarden就搭建完成可以使用了,不过个人还是建议配置数据备份。
先安装7Z,为的是把数据加密打包然后再传到dropbox
wget https://astuteinternet.dl.sourceforge.net/project/p7zip/p7zip/16.02/p7zip_16.02_src_all.tar.bz2 tar -jxvf p7zip_16.02_src_all.tar.bz2 cd p7zip_16.02 make && make install mkdir /usr/local/backup vi /usr/local/backup/backup.sh wget https://raw.githubusercontent.com/andreafabrizi/Dropbox-Uploader/master/dropbox_uploader.sh chmod +x backup.sh dropbox_uploader.sh /usr/local/backup/dropbox_uploader.sh /usr/local/backup/backup.sh crotab -e
backup.sh,这个是用军哥lnmp的备份脚本改的。
#!/bin/bash
#Funciont: Backup website and mysql database
#Author: licess
#Website: https://lnmp.org
Bit_name="bitwarden"
dropboxshell_dir="/usr/local/backup/dropbox_uploader.sh"
drop_dir=/${Bit_name}/$(date +"%Y%m%d%H")
password="wwwwwwww"
#IMPORTANT!!!Please Setting the following Values!
Zip_Dir="/usr/local/bin/7za"
Backup_Home="/usr/local/backup/"
######~Set Directory you want to backup~######
Backup_Dir=("/usr/local/bitwarden")
#Values Setting END!
OldBackup=${Bit_name}$(date -d -7day +"%Y%m%d%H").7z
Old_DROPBOX_DIR=/${Bit_name}/$(date -d -30day +"%Y%m%d%H")
Backup_Dir()
{
Backup_Path=$1
Dir_Name=`echo ${Backup_Path##*/}`
Pre_Dir=`echo ${Backup_Path}|sed 's/'${Dir_Name}'//g'`
tar zcf ${Backup_Home}bit-${Dir_Name}-$(date +"%Y%m%d%H").tar.gz -C ${Pre_Dir} ${Dir_Name}
}
if [ ! -f ${MySQL_Dump} ]; then
echo "mysqldump command not found.please check your setting."
exit 1
fi
if [ ! -d ${Backup_Home} ]; then
mkdir -p ${Backup_Home}
fi
echo "Backup bitwarden files..."
for dd in ${Backup_Dir[@]};do
Backup_Dir ${dd}
done
echo "compass with 7z..."
${Zip_Dir} a -mhe -p${password} ${Backup_Home}${Bit_name}$(date +"%Y%m%d%H").7z ${Backup_Home}bit-${Dir_Name}-$(date +"%Y%m%d%H").tar.gz
rm -rf ${Backup_Home}bit-${Dir_Name}-$(date +"%Y%m%d%H").tar.gz
echo "upload to dropbox..."
${dropboxshell_dir} upload $Backup_Home/${Bit_name}$(date +"%Y%m%d%H").7z $drop_dir/${Bit_name}$(date +"%Y%m%d%H").7z
${dropboxshell_dir} delete $Old_DROPBOX_DIR
echo "Delete old backup files..."
rm -f ${Backup_Home}${OldBackup}password这里填你想设置的压缩包密码
需要注册dropbox(需要f~q)验证邮箱后,进入https://www.dropbox.com/developers/apps建立一个app并生成密钥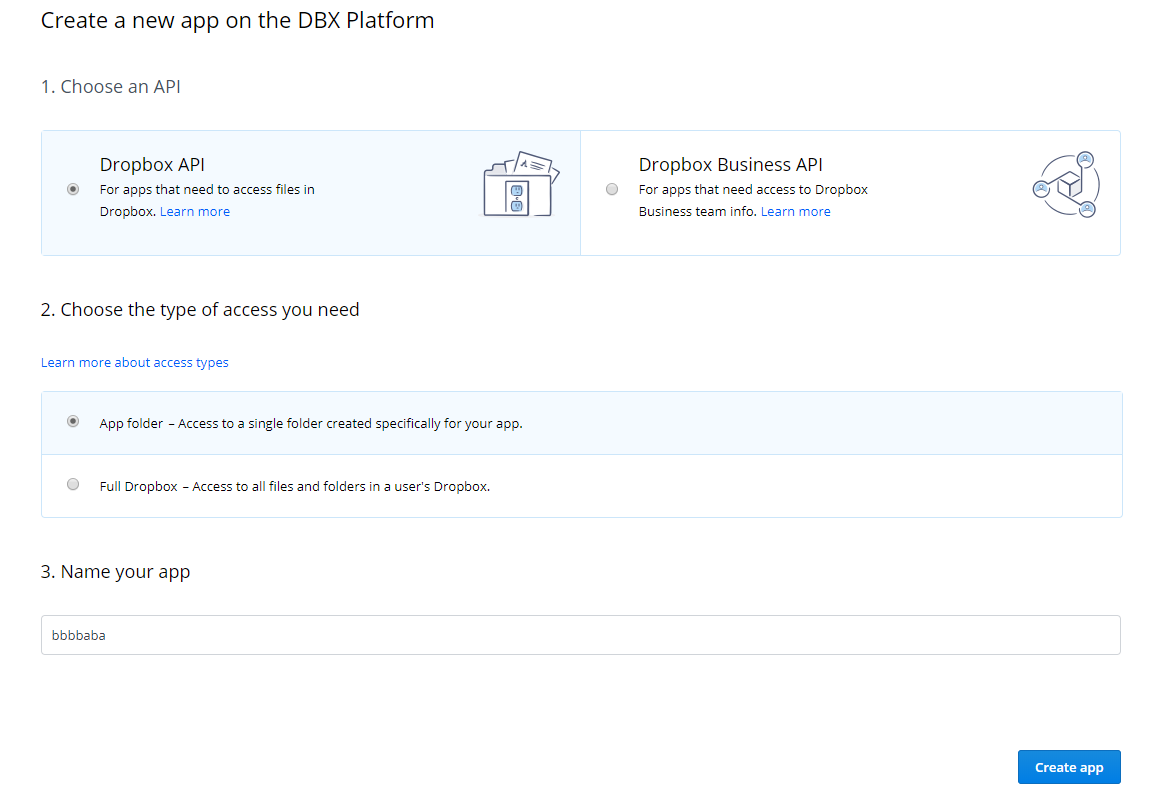
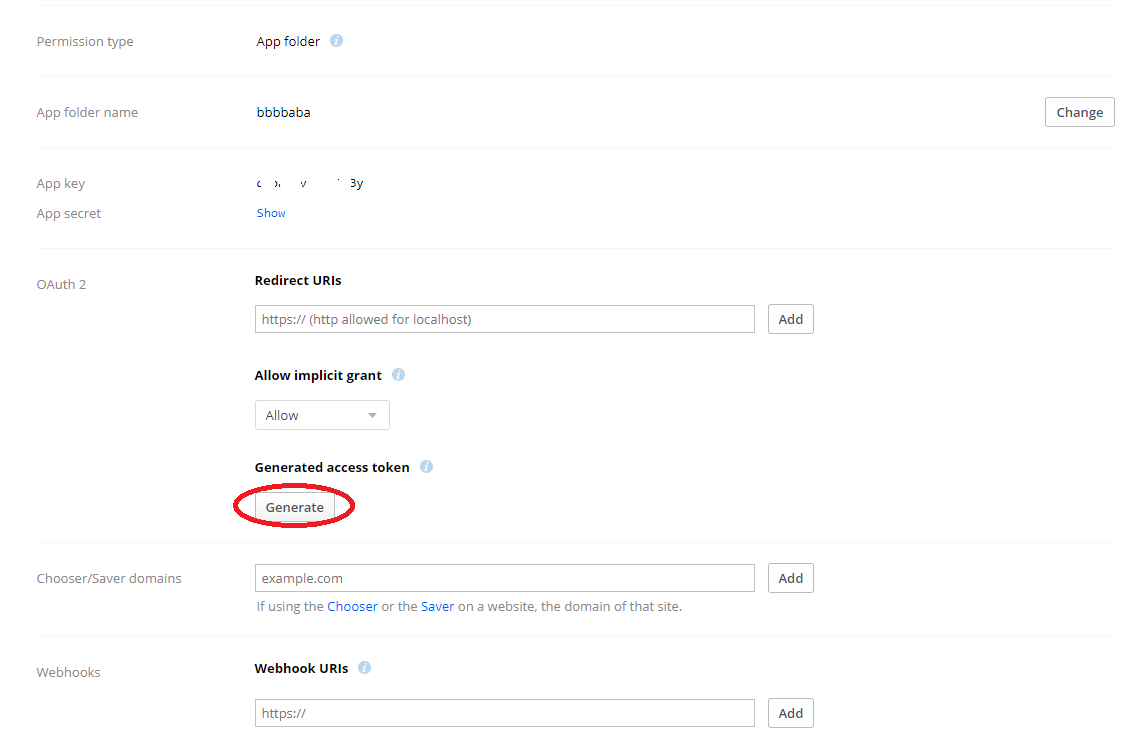
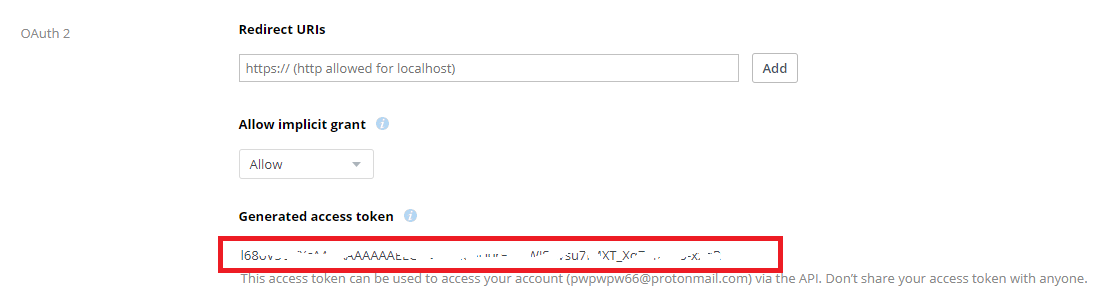
运行dropbox_uploader.sh后将密钥填进去
运行一次backup.sh是为了测试备份是否有效
最后crontab添加定时任务
0 13 * * * /usr/local/backup/backup.sh
0 22 * * * /usr/local/backup/backup.sh
在每天13点和22点备份到dropbox
http://www.virplus.com/thread-368.htm
转载请注明:2019-11-26 于 VirPlus 发表




